Cyber Security Blog “Myths Vs Reality”
The speakers from Cyberia Ireland kicked off by stripping away some of the jargon and explaining in plain English about malware one of the leading cyber threats facing businesses today.
“Malware” is short for malicious software and is a catch all term for software that has been designed to disrupt, damage or gain unauthorised access to a computer system. Common types of malware include computer viruses, adware, spyware and of course, ransomware. More jargon! Cyberia Ireland explained:
Computer viruses have been around now for decades and consist of a contagious piece of code that infects other software on the host system and spreads itself once it is run, mostly when software is shared between computers. Traditionally viruses have acted like a parasite but have been more of an annoyance than causing any material harm.
Adware is software which displays advertisements for the purpose of generating revenue for its author. It checks which Internet sites you visit frequently so it can feature targeted advertising. Not necessarily working with malicious intent, adware becomes a problem when it impacts on your computers performance and can be annoying.
Spyware, as the name suggests, spies on you and tracks your internet activities. It helps the hacker in gathering information about the victims system, without consent. Some spyware, like key loggers, allow criminals to copy login details, passwords, bank details etc. as you type them on your keyboard. Other spyware can turn on your computers webcam or mic allowing a third party to watch or listen in on your activities.
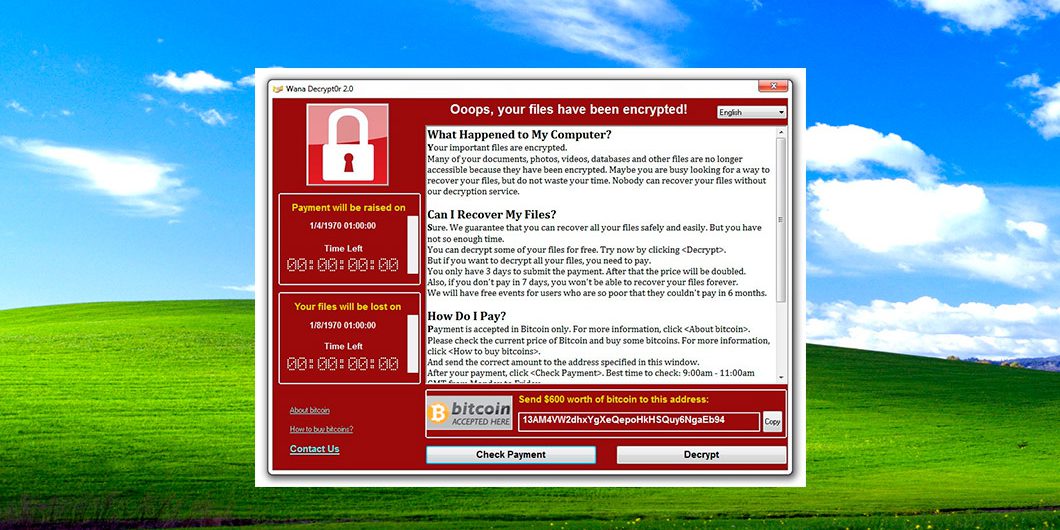
Ransomware is the fastest growing cyber threat currently facing businesses and is an advanced type of malware that restricts access to a computer system until the user pays a fee. Your screen might show a pop up warning that you have been locked out of your computer and a ransom is demanded in order for the restriction to be removed. In some cases, for example with Wannacry which impacted organisations globally last month, including the NHS, documents are encrypted and the ransom is required to get the cryptography “key”.
So armed with all the facts about malware, how can you go about protecting yourself and your business? Cyberia Ireland reluctantly advises that there is no quick fix and no single product that can guarantee to keep you safe from malware. However, ANY genuine security product is better than NONE.
If your system uses the Windows 10 operating system then the new Windows Defender offers real-time, cloud based protection. Use it along with an anti-malware product such as the industry leader “Malwarebytes”. Further advice is to also use a product like “CCleaner” to keep your systems registry in check. Please be careful when downloading any software onto your machines – make sure any programs are sourced from genuine, reputable websites.
Keeping your business safe from cyber threats can seem daunting, but a few simple measures is really all it takes. Getting your anti-malware in place is a good start. Our next blog will outline the other basic measures you can put in place. In the meantime, if you need any further information, you can contact Cyberia Ireland.
Blog Post by Fionna Martin
Fermanagh Enterprise Ltd